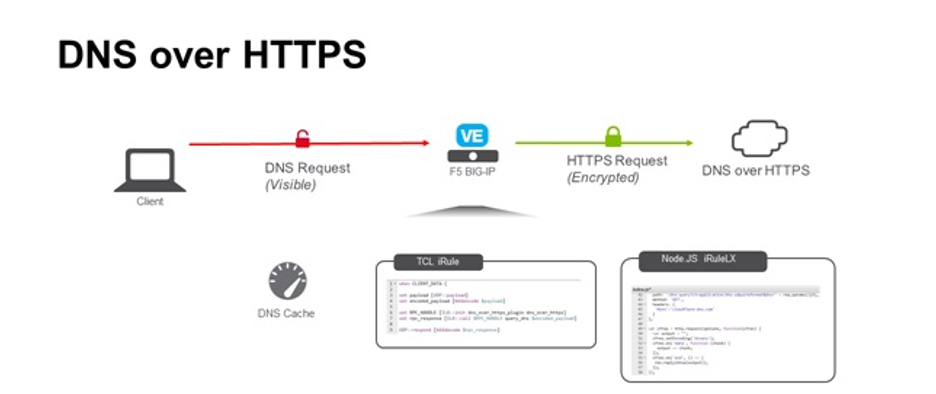
When you enter a web domain name into the address bar (example: www.google.com) of whatever browser you are using. The user agents transmit a request over the Internet to ask for the IP address that particular website. Conventionally, this request is transmitted to servers over the internet. This connection is unencrypted, that makes it easy for third parties to see what website you’re want to access.

However, DNS-over-HTTPS (DoH) do not work in the same way. It transformed this paradigm. for performing remote Domain Name System (DNS) resolution through the HTTPS protocol the DNS over HTTPS (DoH) protocol is used. By using the HTTPS encrypted connections it transmits the domain name you entered to a DoH-compatible DNS server rather than a simple text one (unencrypted) query. This bans third parties from looking into what websites you are wanting to access.
For this, DOH is a best alternative for the DNS. That permits a customer side resolver to transmit the request to an individual resolver and create reactions to request, where the IP & UDP coverings can be replaced completely by HTTPS augmentations. The prime purpose of this protocol is to enhance privacy and security of user by preventing unauthorized parties and manipulation of DNS data by unwanted attacks. Along with additional privacy, second goal of DNS over HTTPS is to enhance the performance.
DOMAIN NAME SYSTEM (DNS)
Whenever you uses a user agent and enters a specific website address, it’s necessarily generating a simple DNS request to the DNS server to get the numeral IP address for that particular website. IP addresses is made of a blend of four unique numbers that make around the three digits long number. They are segregated from each other in sections by periods (for instance, 111.112.113.114). As a response to the user’s DNS request, the DNS server takes the IP address then transmit a response to the User. Onwards, the client exists off the DNS framework and enters in the realm of webserver through the transmission control convention: TCP & HTTP.
Conventionally this exchange of information is done via user datagram protocol. UDP and TCP both of them non-trusted web protocols, which weaker websites which don’t have a reliable and secure SSL/TLS encryption. In what way a “DNS Over HTTPS” is Different from conventional DNS Requests
HOW DNS-OVER-HTTPS (DOH) WORKS?
The DNS-over-HTTPS protocol is recently invented. It was launched back in with a center propose as a web standard a year ago in October. DOH features are already supported by Android. It is planned to be supported by web browsers too. Both: Mozilla Firefox & Google Chrome. DOH is way more reliable than that of traditional DNS for which it’s utilizes a way more secure (encrypted) protocol. Utilizing DNSoverHTTPS reveals that the ISP — and any other third party mentioned before in this article — would not be able to know about certain parts of the DNS searching process because they will be encrypted.
The protocol changed the working of DNS a little. DoH work is a similar way, just like ordinary DNS request, apart from that fact that it utilized Transmission Control Protocol (TCP) for transmitting and receiving requests.
Up till now, DNS queries were generated inform of unencrypted plain text, by an app to the DNS server, by utilizing the DNS settings of the native OS received from its internet service provider. Now DoH encrypts DNS requests, which are referred as normal HTTPS traffic. As you already know, UDP has been launcher for a while now in the “internet” time since the mid-90s. But as web protocols are referred, DNS over HTTPS is comparatively new.
The major difference is that DoH gets the DNS query and transmit it to a DNS server refereed by DOH through an HTTPS connection that is encrypted. These DoH requests are transmitted to exclusive DOH (DSN over HTTP) – capable DNS resolvers (known as DoH servers), which resolve it by with in a DoH request and respond to the client, in an encrypted way.
Because of this, the agencies and associations that depends DoH-refereed items that have been marketing DoH as a strategy for avoidance for ISPs from getting followed, web traffic and for bypassing oversight in prohibited countries. Since the DoH (DNS) query is in encrypted form, it can’t be overruled even by a cyber-security software that relies on passive DNS monitoring to jam quries to known malicious domains.
WHY FIREFOX IS ENCRYPTING DNS REQUESTS
Regardless of the fact that you are searching online from home, at work, while doing anything on your phone, there’s an soft track available for experts who knows very well that how and where they should look. Mozilla has been public about enhancing the privacy and security of internet queries.
Lately in a declaration, Mozilla Firefox emphasized about the centrality of the secured domain framework. Stated Below:
“Because there is no encryption, other devices along the way might collect (or even block or change) this data too. DNS lookups are sent to servers that can spy on your website browsing history without either informing you or publishing a policy about what they do with that information.”
Presently, they could do this by utilizing DOH or by utilizing DNS over TLS. HTTPS represents hypertext transfer protocol and TLS represents transport layer security.
The major contrast there is certainly the port sort that would be used for the purpose of doing transaction. For instance, DNS over HTTPS utilizes port 443, whereas DNS over TLS utilizes port 853. Both of these are reliable alternatives, and honestly many individuals still argue on which technique is comparatively better.
But, Mozilla fire fox has chosen to go with DoH as opposed to DoT stated below:
“We chose DoH because we believe it is a better fit for our existing mature browser networking stack (which is focused on HTTP) and provides better support for future protocol features such as HTTP/DNS multiplexing and QUIC.”
MAKING REQUESTS
Cloudflare offers a DNS over HTTPS resolver at the following address
https://cloudflare-dns.com/dns-query
HTTP METHOD
When making requests via post, the DNS query is also included as the message body of the HTTP request, and the MIME type (application/DNS-udpwireformat) is passed in the Content-Type request header. Cloudflare should utilize the body of message of the HTTP query as the consumer sends, so the text in message body isn’t encoded. When generating requests for getting, the DNS query is encoded inside the URL.. When making requests through the GET, DSN over HTTP query is encoded inside the URL. Another URL parameter of ‘ct’ indicates the MIME type.
THE BENEFITS OF USING DNS OVER HTTPS DOMAIN SYSTEM
DoH increases security by securing domain name, queries from somebody sneaking around on open WiFi, your ISP, or any outsider on your local system. When DOH is activated it makes sure that your ISP cannot collect and sell personal data that is related to your browser search. Because DNS over HTTPS necessarily encrypts the website access requests for consumers through browser.
DOH OFFERS GREATER OVERALL PRIVACY TO CLIENTS
As a rule, DNS looks up through HTTP that fundamentally conceal your browsing history from unapproved access to and keeps information from being gathered by outsiders. This can be exceptionally useful for buyers in nations where web get to is confined.
DOH MITIGATES INTERFERENCE AND MITM ATTACKS
No one likes the thought of some third party spying and snooping into their history and going through one’s unencrypted domain lookups. Then users should be delighted to know that DOH assist in the prevention of parties who may be snooping into their local network, public Wi-Fi, or at some critical ISP level for keeping an eye what sites you’re requesting and any information you share while you are on the connection. This aids is lessening the certainty of middle man attackers from gaining access to your history at the verge of your private information.
DOH LESSEN THE CHANCES OF DNS SPOOFING
DNS spoofing or DNS server compromise happens when any third party or a non-trusted resolver is involved in the communication between the client and the DNS server and alters the response to a phoney IP for the site. This forwards clients to forged sites that seems to be original, by swapping a genuine link with a faulty one.
THE DRAWBACKS OF DNS OVER HTTPS
Numerous experts in the fields of networking and cybersecurity have publicly claimed that many attributes of DoH are a lie. They say DoH is not the ideal user privacy cure that many companies and agencies have been advertising about, for boosting their image as security-first organizations. It all narrows down to user privacy and security. And since privacy is a lead topic, it will continue to be discussed wildly. Blocking or not to block DoH entirely depends on the user. Professional claims that these companies are irresponsible for marketing a half-baked protocol. that doesn’t fully serve its purpose and protect users.
If you looks your DNS for blocking malware or any specific policy, then you will not like what’s next. When activated, DoH will automatically surpass your local DNS server. Through your private browser settings — or your enterprise policies — you can disable DoH.
TRUSTED RECURSIVE RESOLVERS WILL SEE YOUR QUERIES
This protocol is not ideal either. When listing down the advantages of DoH, Firefox also directs to that some of the drawbacks which are that the DNS servers that receives the requests is also able to look into clients requests. Among other DoH sideways — are prohibited from gathering personal identifying data about any of the consumers.
QUERIES GENERATED THROUGH DOH MAY RESPONDS SLOWLY
Mozila Firefox also claims that requests generated via DOH is comparatively slower in response than those made via conventional DOH. They quickly claimed the results of this tested hypothesis shows that DSN over http has the minimal effect or certainly improved the overall response rate and loads a web page for a user.
IS WEB TODAY READY FOR DOH?
Now that users are aware of few technical basics that are significant regarding DOH. Let’s take that into consideration that this protocol is still under experiment and there are many stocks of previous DNS framework that doesn’t comply with encryption. It should be noted that it is not essentially important to update all of the things, however, the updated firefox build added a support for DOH. There is a way to deploy DoH without an OS or browser update, though
WHAT MOZILA FIREFOX IS UP TO MAKE DOH CONVENIENT
In the recent announcement, Mozilla told that they’ve joined hands with Cloudflare as their core TRR “trusted recursive resolver”. Resolvers are actually the ones that resolves domain name request made by users and send responses. So, by using a trusted recursive resolver , what this indicates is that Firefox worked out policy guidelines with Cloudflare being a TRR must be satisfied concerning how information is fetched and stored.
1. Encryption of every DNS requests using DOH
2. Resolving all of DNS requests in a secured manner by Cloudflare being a TRR.
DNS requests passes by Cloudflare’s servers while relying on HTTPS rather than UDP, it indicates that domain quires would be fetched by a reliable entity, and that particular segments of DNS quires will be encrypted.
The name quires passes through many stations. Not all of them are necessarily secured and reliable. By encrypting DNS choirs, it offers better protection to Firefox users.
CONCLUSION
There are a lot of programs and protocols working on right now related to data privacy and website security. Data privacy laws have been wrapping out over the past few years — GDPR, CCPA, NY’s SHIELD Act, etc. DNS-over-HTTPS (DoH) do not work in the same way. It transformed this paradigm.
For the performance of remote DNS resolution through the HTTP protocol. By using the HTTPS encrypted connections it transmits over the domain name you entered to a DoH-compatible DNS server rather than a simple text one (unencrypted) query. This bans third parties from looking into what websites you are wanting to access.
