
Institutions and companies covering every industry across the USA have been affected by an average of 9.5 attacks in 2020 according to IDC and the 2020 DNS Threat Report. This number only demonstrates the central role that DNS plays when it comes to network security because the DNS’s dual capacity are used by threat actors either as a direct objective or a threat vector.
North America ranks #1 when it comes to regional damage brought forth by DNS attacks averaging at around $1,073,000, a slight decrease of 1.36% from last year’s figures. Although there has been a 4% decrease in terms of attack damage in the United States of America, the country still has the highest amount of damage at $1,082,710 when compared to the rest of the world.
The cloud is the main target of attackers. Cybercriminals see hybrid cloud environments as an opportunity due to the number of businesses and institutions that utilize this technology. There is a noticeable growth of 22% in cloud service downtime – 41% in 2019 and 50% in 2020. Could service usage has increased during the COVID-19 pandemic can be enticing for cybercriminals.
The rate of in-house app downtime has also been consistently high: 62% in 2020 and 63% in 2019. DNS attacks has caused application downtimes suffer the most, whether in-house or in the cloud. According to the survey, 82% of the companies has experienced these application downtimes.
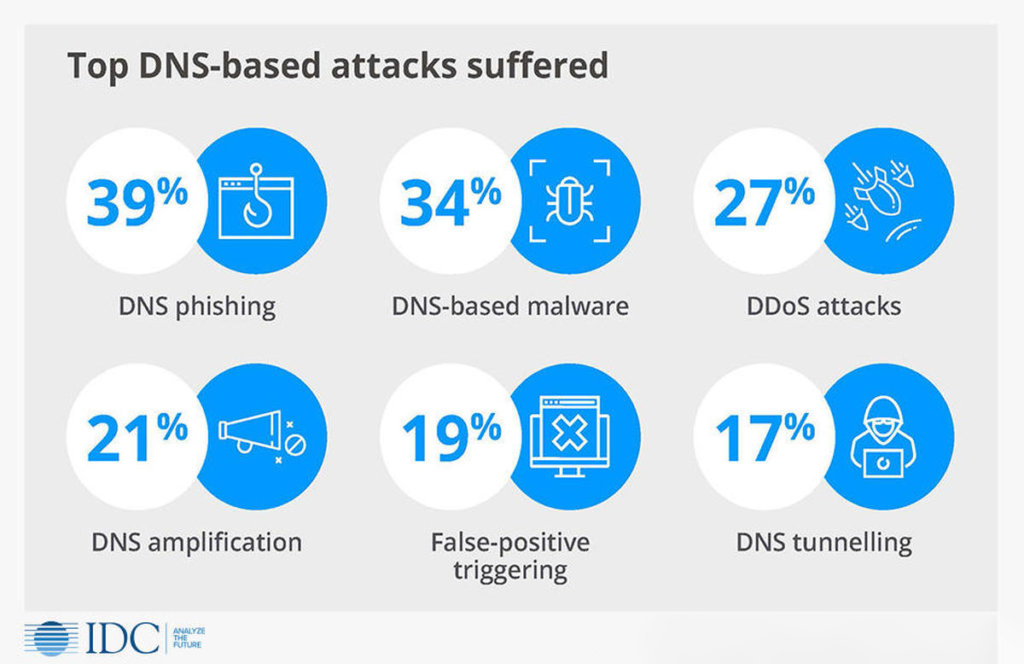
The 2020 DNS Threat Report also revealed the wide scope and changing methods of cyberattacks that span from low signal to volumetric. Phishing is the most popular attack type; 39% of the companies surveyed say they recorded phishing attacks. Malware-based attacks followed at 34% while traditional DDoS are at 27%. There was also an increase in DDoS attacks, 64% or almost two-thirds are over 5Gbit/s.
Although these numbers are a cause of worry, the good news is that the awareness level of companies to fight and prevent these cyberattacks is also increasing. In the 2019 report, 64% of the companies saw the importance of DNS security when it comes to network structure. This year the percentage increased to 77%.
Also, there has been maturity in the usage of Zero Trust strategies. The report also revealed there is also been a 10% increase of predictive analytics: 45% last year to 55% this year.
Romain Fouchereau, IDC’s Research Manager European Security says, “Recognition of DNS security criticality has increased to 77% as most organizations are now impacted by a DNS attack or vulnerability of some sort on a regular basis.”
“The consequences of such attacks can be very damaging financially, but also have a direct impact on the ability to conduct business. Ensuring DNS service availability and integrity must become a priority for any organization,” he also added.
Possible hackers use the underutilized information provided by the DNS. The 2020 DNS Threat Report disclosed that compared to 30% in 2019, 25% of the organizations in 2020 admitted that they do not conduct DNS traffic analytics. Also, 35% of the companies conduct no filtering via internal DNS traffic. Only 12% of the companies that were surveyed gather their DNS logs and tally them via machine learning.
Ronan David, VP of Strategy for EfficientIP, says, “In this era of key IT initiatives like IoT, Edge, SD-WAN and 5G, DNS should play a much larger role in the security ecosystem.” He further underscored the significance of DNS information in creating a strategy that blocks against attacks made by potential hackers. “The pandemic has exacerbated the need to shore up DNS defenses, when any network or app downtime has major business implications,” he adds.
The attack protection of any company can be improved through User Behavioral Analytics and threat intelligence. SOCs and SIEMs can be fed with a DNS security solution. Through DNS data, an organization can easily come up with simple methods to detect attacks and implement necessary solutions. The 2020 Global DNS Threat Report also notes that 29% of the organizations that were surveyed use SIEM software to recognize compromised machines and devices. Compared to 22% in 2019, 33% of the surveyed companies transferred DNS info to SIEM analysis this year.
