
The Expect-CT header distinguishes certificates issued by unauthorized Certificate Authorities and forbids them from issuing so. It has been launched for prevention of miss-used and forged certificates for the sites from going unnoticed. It detects Websites are required to prove their certificates that have been logged to CT by providing Signed Certificate Timestamps (SCTs). The Expect-CT header tells you if you are fulfilling this compulsion. From July 2018 (Chrome 68), Google Chrome don’t trust any SSL certificate that does not obey the aforementioned Certificate Transparency Policy: that means that, if your certificate is not listed, your consumers and visitors will be notified by a security alert.
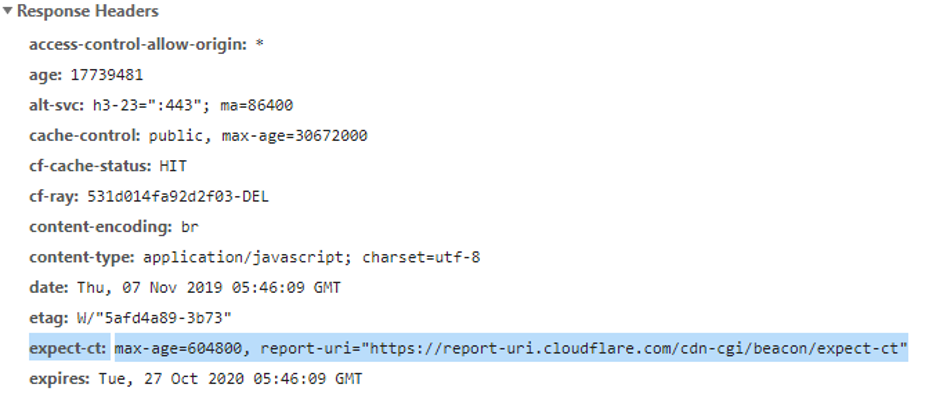
Web hosts which oblige the Expect-CT header are remembered by the User agents as defined Expect-CT Hosts. The user agent monitors every connection to any Expect-CT HTTP Host for intended deployment with the user agents’ Certificate Transparency Policy. If the connection unable to fulfil the CT Policy, the UA transmit a report to a URI configured by the Expect-CT Host and fails the connection, depending on the configuration that the Expect-CT Host selects.
In the case of misconfiguration an Expect-CT can cause trouble of connection failures. The operators are recommended to comply Expect-CT along warnings, by utilizing the reported specification & gradually escalating time period for which the user agent keep the host in memory. All these mentioned precautions can aid web operators in gaining confidence that the Expect-CT compliance isn’t the reason which causes unwanted failures of connection. The first-time a User-agent connects to a host; it lacks the necessary information.
Why Browser Security Headers should be used?
Security of a website is as significant as its content and SEO. Numerous websites are hacked because of misconfiguration or lack of security. Browser Security Header assist in defining that a set of security prevention should be enabled or disabled on the browser. And for reinforcing the protection of your web browser securing it from unwanted attacks and to minimize its vulnerability register) it’s a forged one and that site is not reliable. They prevent the use of mis-issued certificates for websites.
Certificate Transparency (CT)
CT, as you might already know, stands for Certificate Transparency. An open framework developed by Google for monitoring and checking the certificates issued by Certificate Authorities in the near past. CT has been around for a time now, but Chrome is going to need that all certificates issued past in October 2017 and afterwards will have to be logged in CT logs unless they won’t be validated. It is more like an open-data register that can be utilized by all the CA to log all certificates they generate and issue: by cross-checking that register, webmasters and site owners will be able to segregate wrongly issued certificates and secure their website – and their consumers – from forged and misused certificates and/or scoundrel agencies.
If your website is accessible by Google Chrome and any other Chromium-based browsers today, you are not supposed to worry as you’re already inside CT-compliance. With the addition of Expect-CT header, it sets a validated certificate policy framework for a website and boots its reputation.
BACKGROUND INFORMATION
CT logs are developed upon the biases of the Merkle tree structure. Nodes are tagged with additional cryptographic hashes to their sub-nodes. The Leaf nodes attain hashes of actual chunks of information. The labeled parent node, depends on all of the other nodes that tree contains.
The contextual background of certificate transparency (CT), the data that is hashed with leaf nodes are the validation certificates that various CAs operators has issued. Those Issued Certificate are verified by an audit-proof that can be issued and verified competently, in logarithmic O period of time.
How CT Logs Work
The Certificate Transparency Logs can be easily accessed by the general public. Therefore, administrators can monitor them and search for their domains. Here a quick look at the Certificate Transparency log mechanism. Three components are required to come together for CT to work:
- The Submission of certificates to logs.
- Checking of the logs
- Auditing, which is done by built-in auditors in User agents
Besides, it is also recommended that site owners should add the Expect-CT header to their responses. Browsers get to decide whether the certificates presented to are valid or not. Apart from certificate, browsers monitor the Signed Certificate Timestamp (SCT). This data has the timestamp when certificates were issued.
DIRECTIVES of HTTP EXPECT-CT HEADER
Expect-CT header is being utilized for monitoring your certification have been appropriately listed: then can be implemented easily with very little need of configuration. And can be listed in two distinct operating modes: report-only (the default) and enforce. Following is the whole list of available directives of expect-CT header:
Enforce: It is optional directive for monitoring whether the browser should enforce the policy or can be treated as the report-only mode. It signals to web browser that acquiescence with the Certificate Transparency policy needed to be enforced. The directive lacks value so it all up to you if want to include it entirely depends on if you want the web browser to enforce the policy or just pass on the report to the user.
max-age: This most needed directive determines the exact amount of seconds that users web browser is supposed to cache and then apply the responded policy, no matter it is enforced or on report-only mode. If a cache receives a value bigger than it should represent, or if any of its subsequent calculations excess, the cache will consider this value to be either 2,147,483,648 (231) or the bigger positive integer it is supposed to represent.
The max-age directive is needed own a specific directive value, for which syntax body is as followed:
Expect-CT: max-age=86400, enforce Expect-CT: max-age=86400, enforce, report-uri="https://foo.example/report" Expect-CT: max-age=86400, report-uri="https://foo.example/report"
report-Uri: the absolute URL where the browser supposed to send a report of Expect-CT failures.
This required report-URI directive is needed to have a value that is discreet. For which body of syntax is given below:
Report/URI/value = absolute/URI
When the optional report uri directive is present with the enforced directive, the configuration is known as “enforce-and-report” configuration, alarming the web browser that acquiescence to the Certificate Transparency policy is supposed be enforced and the failures should be responded.
The general requirements for all directives are given below:
- The order in which directive appears is not important.
- The given directive should not be appeared more than single time in the particular field of header. Directives are either optional or default, as specified in their descriptions.
SUPPORTED BROWSERS:
The browsers are that’s are supports HTTP Expect-CT header are listed down:
- Google Chrome
- Opera
Browsers will not validate an Expect-CT policy unless the website has ‘proven’ it is in the form of a certificate satisfying the certificate transparency requirements.
All of the Browser implementations regarding the type of CT logs that can be for the certificate.
GETTING STARTED
For getting the start, like every other new mechanism, all sites should deploy it in the report-only mode for purpose of testing. And make sure it isn’t going to cause crashes.
Expect-CT is secure, convenient and is able to give you important information about your web site. All you need to do to is simple setting of the following HTTP response header on web site:
Expect-CT: max-age=604800, report-uri=https://{subdomain}.report-uri.com/r/d/ct/enforce
To install this header on your website you will need to update the subdomain in above-mentioned example to your own web site’s subdomain.
VALIDATION OF THE CONFIGURATION OF EXPECT-CT
Expect-CT’s security feature enables a site developer and operators to be charge of how CT is analyzed on basis of their properties. Its core function is to activate CT deployment, redirecting web browsers for sending reports regarding issues validating a site’s certificate. The Expect-CT is technically similar to HSTS; when you deploy a policy you particularly limits its time duration, and so web browser can save it so it can remember it for any time in future when the user visit that web site again.
While transitioning, reporting will proved to be beneficial as it provides user authentic detection of invalidated web sites. It’s something user agent would monitor now so that you’re not trapped by any pop-ups and alarms when Google Chrome starts to enforce CT. It is also beneficial when someone tries to use a fraudulent certificate for unauthorized properties.
SERVER PROCESSING MODEL
Expect-CT Hosts uses the model which implement two basic segments:
- The processing model for HTTP quires received over a trusted transport
- The processing model for HTTP request received over non-trusted transports.
EXPECT-CT CONNECTIONS EVALUATION FOR CT COMPLIANCE
When a web browser connects to a valid Expect-CT Host by relying on a TLS connection, if the TLS connection failure occurs, the UA MUST dismiss the connection by not allowing the user to move further. But in case the connection has zero failures, then the User-agent will run another correctness run deploying CT Policy. A User-agent’s compliance should be evaluated with respective CT Policy while connecting to a Expect-CT Host. It is also acceptable to pass this CT compliance run for few hosts but that totally depends on local policy. For instance, a user agent may unable CT deployment runs for those hosts having validated certificate dismisses at a user-defined secured anchor, instead of the secured anchor native to the user agent.
The Expect-CT Host gest expired if the respective expiration date indicates any date from the past. The User-agent is supposed to ignore any terminated Expect-CT Hosts in its cache memory and should not treat those hosts as Known Expect-CT hosts. If a connection to a Known CT Host overrules the UA’s CT policy (i.e. the connection is not CT-qualified), and if the Known Expect-CT
The Host’s Expect-CT metadata shows an “enforce” configuration, the User-agent MUST treat the CT compliance invalidation as a non-recoverable error.
If the connection to the CT Host overrules the user agent’s policy, and if its Expect-CT metadata contains a “report-URI”, the User-agent is supposed to send report to “report-URI”. A user agent that has noted a host in past as Known Expect-CT Host should evaluate CT compliance while organizing the TLS session, prior initiating the HTTP conversation while relying on the TLS channel. If the user agent does not get CT compliance evaluated, the reason is that the user has elected to deactivate it, or may be the presented certificate chains up to a user-defined secure anchor, user agents are not supposed to send Expect-CT reports.
WHERE IS THE RISK?
If you got a certificate that issued to your website before the mentioned date of April 2018 in then Google Chrome is unable to enforce, certificate transparency rules. Else, there will a large number of valid certificates that are no longer valuable, irrespective of the fact that they were issued before CT was invented. But, if you have enforced the Expect-CT header and relies on max-age directive for caching the browser. Certificates that are unable to reach the CT outlined requirements are not supposed be accepted regardless of the fact that they are stamped before referred date. By this way, they eliminated the chance of older certificates determined to get validation.
REPORTING OF EXPECT-CT HTTP FAILURE
While the user agent tries to connect a Expect-CT HTTP Host with a CT unqualified connection, the user agent sends Expect-CT failures to the report-URI, in the Expect-CT Host’s metadata. And in the case the user agent has not already transmitted over an Expect-CT report for the unqualified connection, then the user agent is supposed to configure report-URI, if any about Expect-CT failures.
CONCLUSION
Security of a website is as significant as its content and SEO. Numerous websites are hacked because of misconfiguration or lack of security. The Expect-CT header distinguishes certificates issued by unauthorized Certificate Authorities and forbids them from issuing so. CT resembles an open-data register that is being used by all the CA to log all certificates they generate and issue. It has some derivatives for this purpose. HTTP Expect-CT header has been launched for prevention of miss-used and forged certificates for the sites from going unnoticed. Several browsers support it.
